
How To Automatically Merge GitHub Security Updates
Managing security updates on GitHub can get hectic in a hurry as third-party dependencies develop at their own pace, separate from your project.
Leaving vulnerable dependencies unpatched can open your entire application up to otherwise avoidable threats, but manually reviewing and merging such updates can quickly eat up all of your time. As with so many redundant tasks, automation is the answer.
Automation expedites the drudgery of reading vulnerability descriptions for individual dependencies within GitHub's dependency review interface and makes merging approved dependencies a snap.
Continuous integration processes rely on dependable automation. This applies to all facets of development where code is regularly updated or altered by multiple contributors. However, it’s especially important for automation to run smoothly with security updates.
GitHub provides powerful tools to help developers keep up with dependency vulnerabilities, including automated utilities such as Dependabot. Read on to learn how Dependabot works and what Mergify can do to make it better for your development process.
Using Dependabot to manage GitHub security updates
An application's code can change constantly as it evolves and projects that provide useful features can come to affect a large number of applications that depend on them to function correctly.
Keeping applications with long lists of dependencies up to date and secure can morph into a full-time job if handled manually. Luckily, GitHub's Dependabot can automatically monitor your repository for vulnerable dependencies. You can quickly activate Dependabot security updates in your own repository's settings, under "Security & analysis."
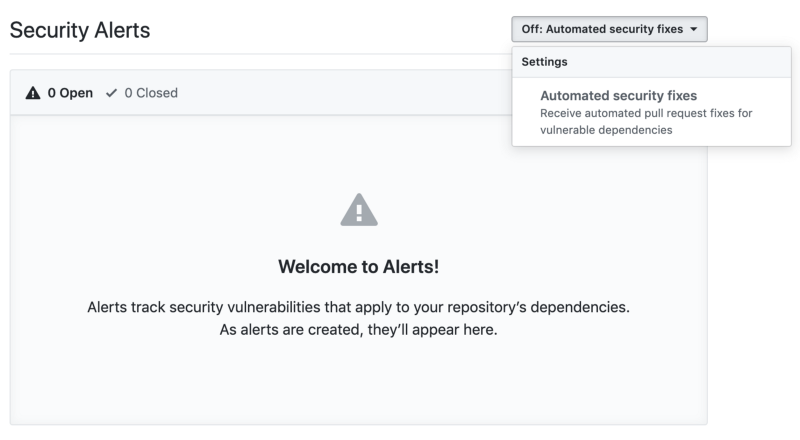
Whenever a dependency is found to be vulnerable, Dependabot can be triggered automatically to generate a fresh pull request and link it to the original alert. This instantly provides project administrators with contextually transparent pull requests for third-party vulnerabilities.
To accurately monitor your repository's dependencies, Dependabot keeps track of your dependency graph. This file is a summary of both your project's manifest and lock files. Both dependencies and dependents are summarized within your repository's dependency graph. Both direct and indirect dependencies are tracked in this file.
Once activated for your repository, the dependency graph is automatically populated and updated with each push to your or any linked repository. Not all package managers and formats are fully supported by GitHub's dependency graph, so the accuracy of your own may vary.
Dependabot generates pull requests that are designed for easy reviewing and merging. Contributors with full access to Dependabot alerts for your repository can review vulnerability details and more before merging the pull request. However, especially as your repository grows in complexity, it can help to process these types of pull requests automatically. Dependabot no longer supports automatic merging natively, but Mergify can help with this.
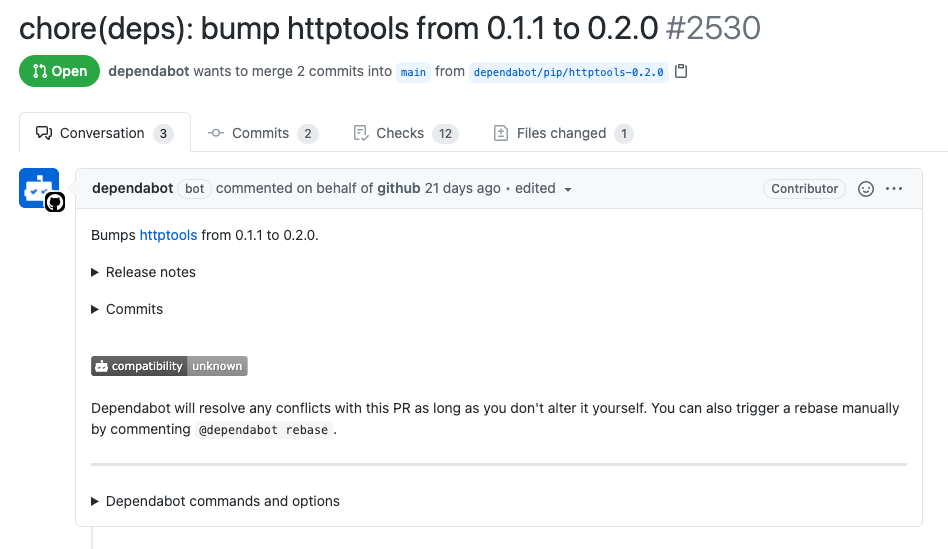
Merging GitHub security updates with Mergify
Mergify supports automating the pull requests Dependabot creates for your repository. You can quickly configure Mergify to merge commits into your primary repository once each pull request has made it through your CI system, eliminating the hassle of manually reviewing and merging them one at a time.
To set up automatic merging of Dependabot pull requests, you only need to create a pull request rule in your .mergify.yml file. This rule will then define how and when new pull requests should be merged. The code for this is as follows:
pull_request_rules:
- name: automatic merge for Dependabot pull requests
conditions:
- author=dependabot[bot]
- status-success=Travis CI - Pull Request
actions:
merge:
method: mergeThe value you choose to use for the status-success parameter should match the name of your chosen CI system (“Travis CI” was chosen above). With dependabot specified as the author of the request to be auto-merged, the above rule should run unsupervised, keeping your repository secure without adding to your workload.
Tips to troubleshoot GitHub security updates and automated merging
If you need a bit more control over the GitHub security update merging process, the following tips might be useful.
Troubleshoot Dependabot errors
Although Dependabot generally creates clean pull requests, it can sometimes run into errors. When this happens, it will post the error in question on the alert that triggered its pull request attempt. To take a closer look at the alerts Dependabot has generated, you can access them from the Security tab for your repository on GitHub.
In certain circumstances, you might not get any security update. There might be an issue with your dependency listing file — read here on how to debug Dependabot security updates.
Limit auto-merging to approved pull requests
If you need to limit automatic merging within Mergify to pull requests that have already been reviewed and approved by a specific contributor, you can do so by adding a new approved-reviews-by condition to your Mergify configuration. To enable such functionality for merges approved by a user named gr8guy, the previous code example would become the following:
pull_request_rules:
- name: automatic merge for Dependabot pull requests
conditions:
- author=dependabot[bot]
- approved-reviews-by=gr8guy
- status-success=Travis CI - Pull Request
actions:
merge:
method: mergeAuto-merging GitHub security updates can be easy
With Mergify and Dependabot working together, your pull request reviewing and merging process can be drastically improved. Say goodbye to endless lists of pending pull requests by activating lightning-fast merging automation today.



